From 02.03.2020 – 05.03.2020 the Building IoT conference took place in Essen (Germany). We took part at this conference dedicated for software developers in the IoT domain. The main topics of this year were testing and security.

The keynote speech of the conference was held by Alexandra Schladebeck (@alex_schl), CEO of BREDEX GmbH. She presented what testing in the IoT context means. Quality assurance and the role of testers in this context is not so easy as the real world with all its manifestations must be considered. A simple example: When someone is cancelling the 05:30 am alarm of an Echo in a whisper, it’s probably because they don’t want to wake up their partner. Alexa should not confirm the cancellation at a volume louder than the alarm would have been. In IoT, the current circumstances must be considered. Software issues that are tackled with a reboot of the whole system are critical. IoT devices may not always have connectivity. What if, after a reboot, the software issue is still not solved and an update has to be retrieved in order to get the connected car running again? These were only some examples Miss Schladebeck brought up. In order to guarantee high quality, testing must be part during development period. When new features are requested, one not only should think how to implement it in the existing system but also how this can be tested. Another question that should arise: “Does it bring new risks and are the added values really worth to have these risks? The real world is too diverse in order that there exist tests for everything in advance. Therefore, automated tests must be added continuously after bringing a system to production.
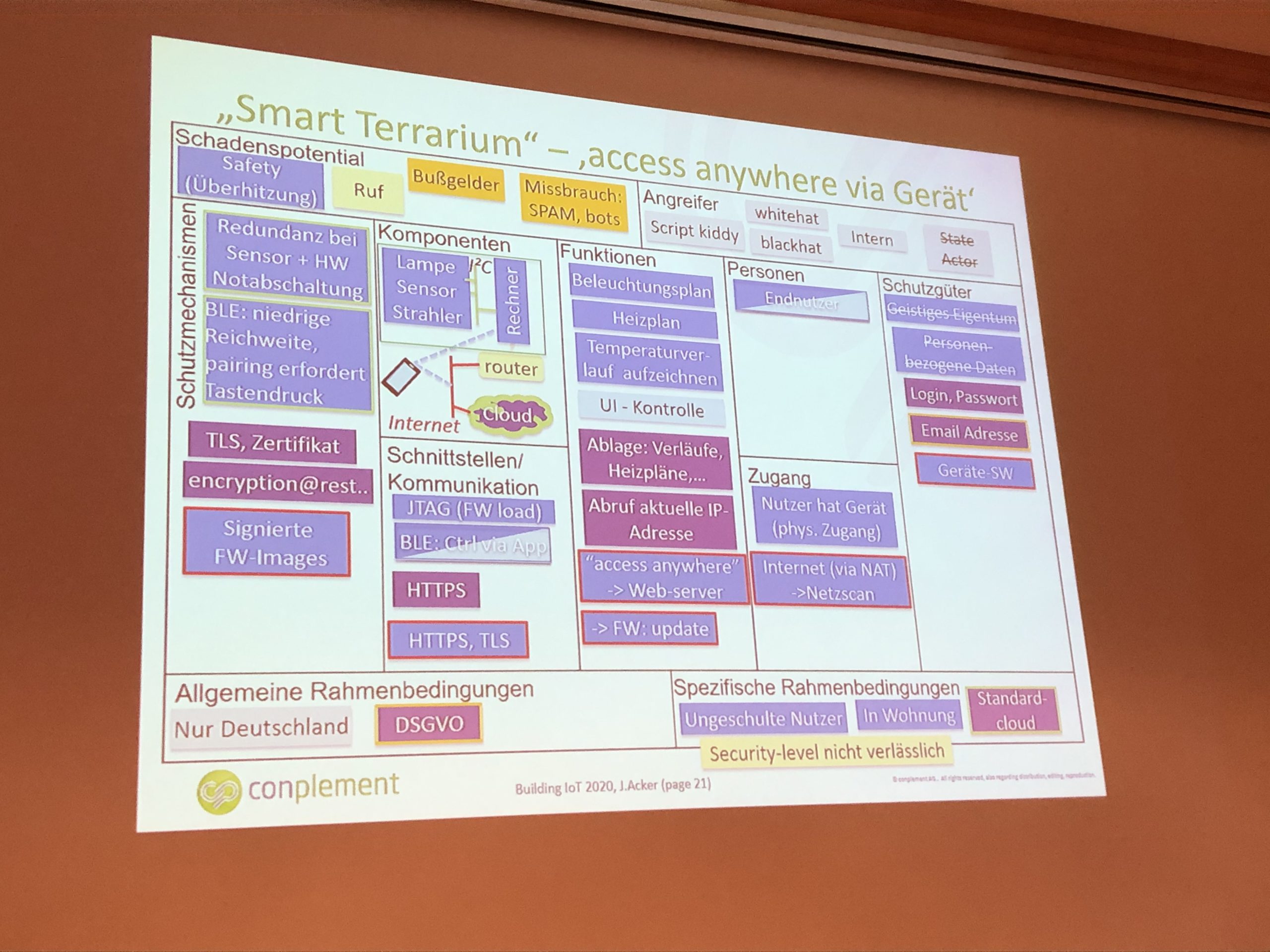
Jürgen Acker from conplement AG presented an interesting idea in his talk “Security Canvas or speed boat instead of a cumbersome risk analysis”: The security canvas. Like the business canvas does it in the business context, the security canvas can provide a general overview about security regarding a project. With the security canvas, the security implications adding new features can be shown up in an easy and understandable way. It does not aim to replace a deep dive into securing a system.

More and more devices become part of the internet. Having unsecure IoT devices leads to huge problems. Security is an important topic in IoT. When developing software for the IoT domain, there exists specifications that should be taken into consideration. Sebastian Fischer, from Frauenhofer AISEC, provided a good overview what specifications exist:
- OWASP IoT Project
- DIN SPEC 27072 (will be replaced by EN 303645)
- EN 303645 (draft)
- Law defined in Great Britain (draft)
The OWASP IoT project (https://owasp.org/www-project-internet-of-things/) helps to understand the security issues associated with the Internet of things. Every developer working on IoT projects should know the top 10 IoT security problems so that he can make sure that these problems cannot happen with his IoT solutions. The DIN SPEC 27072 provides guidelines regarding security for IoT consumer products. In Europe and Great Britain an expert group is working on a guideline for general IoT products. The first drafts are available online.
These are only guidelines that the manufacturers should consider during the development of their IoT products, but currently it is not mandatory to follow these guidelines.
Another interesting talk was held by Richard Cassidy: “Securing IoT with Entity Analytics”. Currently the user behavior is heavily analyzed on the internet. When it comes to IoT or even OT, fewer is analyzed. It takes on average 5 minutes it takes for an IoT device to be attacked once connected to the internet (source: NETSCOUT’s Threat Intelligence Report https://www.netscout.com/sites/default/files/2019-02/SECR_001_EN-1901%20-%20NETSCOUT%20Threat%20Intelligence%20Report%202H%202018.pdf). He suggests to think how hackers think. Use analytics to detect anomalies: when at some point in time, the device opens a new port, or when the device behaves differently than normally, or when it sends data to another endpoint, …
Once the IoT devices are no longer updated, existing security vulnerabilities remain and can be exploited by hackers. This was interesting point that was also presented at the Building IoT conference: the guarantee time for IoT devices. How long should IoT devices get updates? Currently there is no law that defines it. A user most probably will not recycle an old device when the device is still working but there are no new software updates. It is very difficult to guarantee security updates for several years. Consider the case when for the currently used encryption method a major security leak is found. Exchanging the existing encryption method with a new one is not an easy task.
Other interesting ideas and presentations we saw at the conference are:
- On Wednesday there was an interesting presentation regarding connected cow use case. Make a remote software update on the connected cow sounds strange, but in the future this will be a standard case.
- Marcel Kurovski, Data Scientist at Inovex, presented deep learning on the edge with Google edge TPU to smart badminton: An existing IoT project (baddy) was connected with AI that challenges the badminton player. In this presentation the Tensorflow model was broken down to a very tiny model without loosing precision.
- Martin Stolz (elastic items GmbH) presented his learnings when making first IoT prototypes to a hardware product. Very good and practical learnings
- Continuous deployment of microservices on IoT devices on the edge
- Taking into consideration the wrap up time of a programming language when using serverless functions – a lot of time (and therefore money) can be saved when considering this fact.
Concluding, the Buiding IoT conference was an interesting conference. Not only because of the talks but also the people attending this conference. I met well known faces, doers from which I can learn, but also people that are not yet deep into IoT. From latter case I learned with what topics they struggle. We plan to share our knowledge regarding IoT. More will follow soon.



